Scanning an AWS S3 Bucket for Malware with Zero Code
In 2014 AWS announced Event Notifications for S3. Event notifications allow you to receive notifications whenever actions take place within an AWS S3 Bucket.
Specifically, we can receive a notification whenever a new file is uploaded to an S3 bucket
(Known as s3:ObjectCreated:*, in the documentation). When a file is uploaded there are
several actions available but the most interesting is to run an AWS Lambda Function.
With our Lambda function, we can automatically send a request to AttachmentScanner, scan the file for Viruses, Malware, Phishing or other Malicious files and then take action if the AttachmentScanner AntiVirus API finds a match.
Scanning your S3 Bucket
With the AWS Serverless Application Repository, it's possible to deploy our Lambda function to use with your S3 Bucket, with zero code required and just a few clicks.
Installing the Serverless Application
There are two options to install the application. You can either use the source code or you can use the Serverless Application Repository. Here, we're going to use the repository:
First, head to the Serverless Application Repository and then press "deploy".
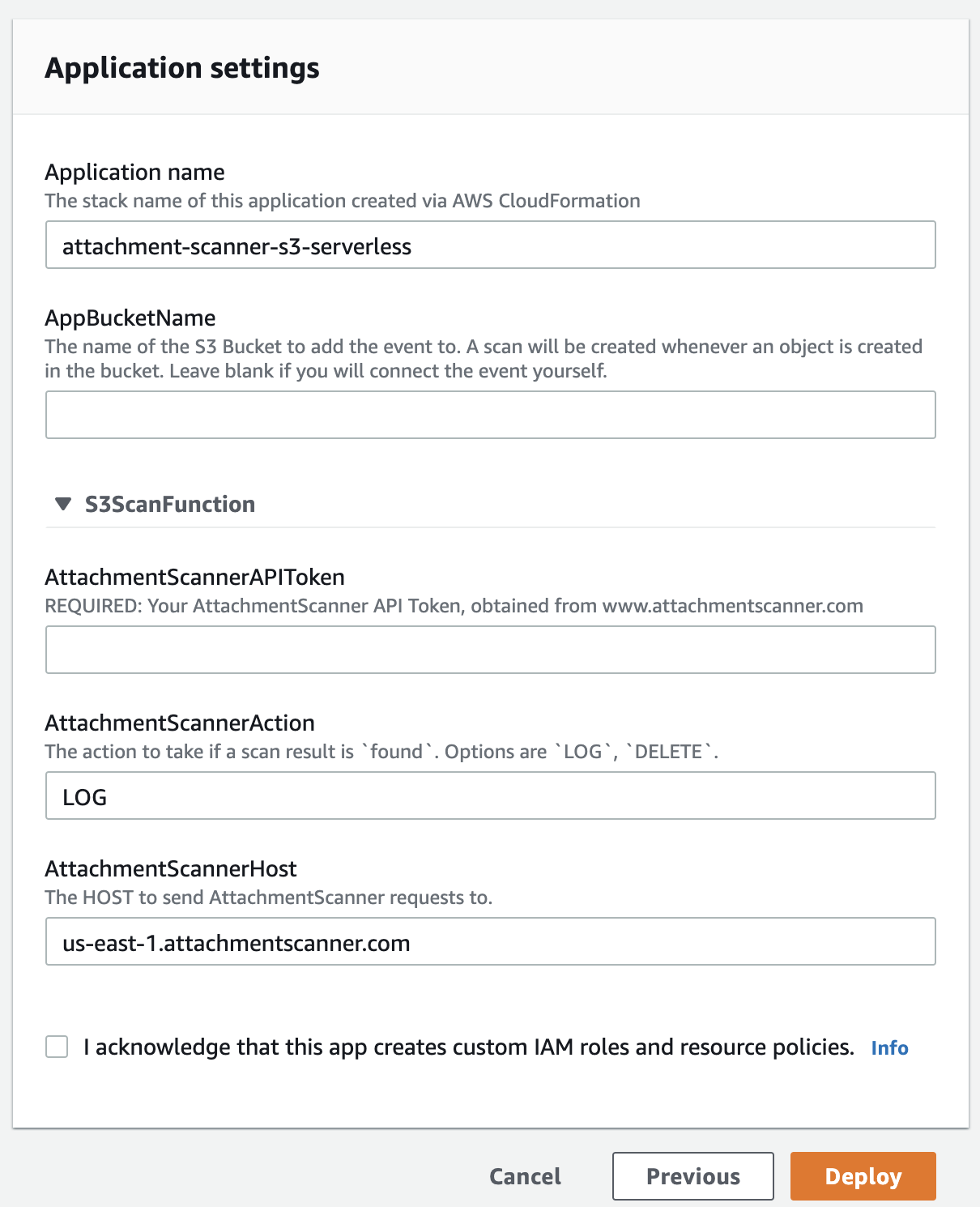
Make sure that the region in the top right is the same region as your S3 Bucket otherwise deployment will fail.
From here you'll be prompted to set the following:
- Application Name - this will be the name of the CloudFormation stack used under the hood (prefixed with serverless-)
- Your Attachment Scanner API Token (contact us if you need a free trial to test things out).
- The name of your S3 Bucket you wish to scan (Make sure it's in the same region as the application you're creating).
- The action to take if malware is detected in the S3 Bucket.
- You can also set a different Attachment Scanner Host if you want to use our Europe or Asia Pacific regions instead of the US API.
Currently, we support the following actions:
| Action | Description |
|---|---|
| LOG | The default action. No action occurs when malware is found. Results are logged to AWS CloudWatch. |
| TAG | Tags objects in S3 with scan ID and result (as-scan-id & as-scan-status). |
| DELETE | Any malicious files are automatically deleted from the S3 Bucket. |
Once you've chosen your options and agreed to allow custom IAM roles and policies (these are needed to allow access to the bucket and create the trigger) click "deploy" again.
That's it, you should be setup and ready to scan any uploads to the S3 Bucket for malware.
Testing the Installation
Now that the serverless function is setup we can upload a file to S3. We recommend using the Eicar File (You can read about it here: What is the Eicar File).
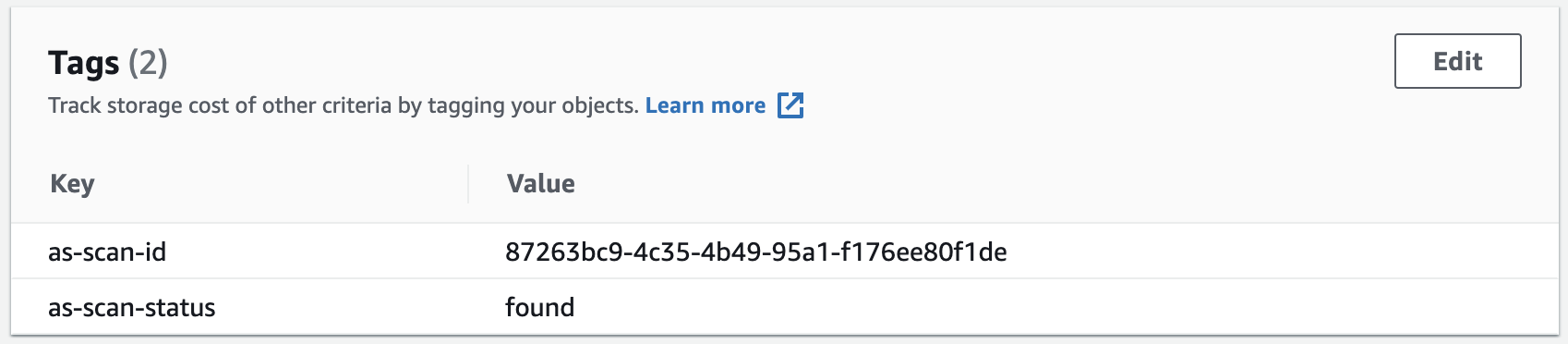
Shortly after the upload lambda function will send a temporary URL to Attachment Scanner.
In this instance, we used the TAG action, which has added the scan ID and
a found scan status.
Checkout the code
We'll shortly be writing another aticle detailing exactly how the lambda function works. However, for now you can check out the source code to see how things work. Feel free to send us a pull request with any new features too!




